Documentation
CloudBasic:
- What is CloudBasic:
- Most common scenarios:
- Using CloudBasic:
- Prerequisites
- Limitations
- Supported MS SQL Server Versions
- Deployment Guide (PDF)
- Release Notes
- Get Started - Configure Multi-AZ or Multi-AR with Readable Replicas
- SQL Server to SQL Server Replication
- SQL Server to Redshift
- SQL Server to S3 Data Lake
- Monitor a Continuous Copy Relationship
- Promote RDS/SQL Server Read-Replica to Primary
- Terminate a Continuous Copy Relationship
- Logs and Errors
- Warnings
- How To Upgrade
- Updating your version
- CloudBasic advanced features:
- Working in AWS:
- RDS Assemblies Activation Test
- RDS/SQL Server User Management
- RDS/SQL Server Backup and restore from/to S3
- RDS/SQL Server Snapshot-Restore
- VPN/VPC - Replication over VPN/VPC
- Compare Instance Types (Features & Support Details)
- How To Extend the Default Data Storage
- Attach IAM Role to EC2 and Redshift Cluster
- Deployment guide:
- Additional topics:
API Documentation:
- Default API Configuration
- Instance Management:
- User Management:
- Replication Management:
- CreateReplication
- CreateAllReplication
- GetReplicationsList
- ReplicationStatus
- AlterReplication
- DeleteReplication
- StartReplicationService
- StopReplicationService
- AnalyzeReplication
- CreateRedshiftReplication
- AlterRedshiftReplication
- DeleteRedshiftReplication
- CreateS3Replication
- AlterS3Replication
- DeleteS3Replication
- GetLogs
- RebuildDbReplicaIndexes
- RebuildDbReplicaIndexesStatus
- ReseedTable
- ReseedTableStatus
- Multi-AZ HA Cluster Management:
- Lambda/node.js Example:
- Disaster Recovery & No-Downtime Migration Management
- Service Management:
Attach IAM Role to EC2 and Redshift Cluster
The recommended way to authorize access to S3, Redshift and SES is to attach an IAM role, with properly granted permissions, to the CloudBasic EC2 instance (pair of instances if operating a CloudBasic Multi-AZ HA Cluster) and associate the IAM Role with the Redshift cluster.
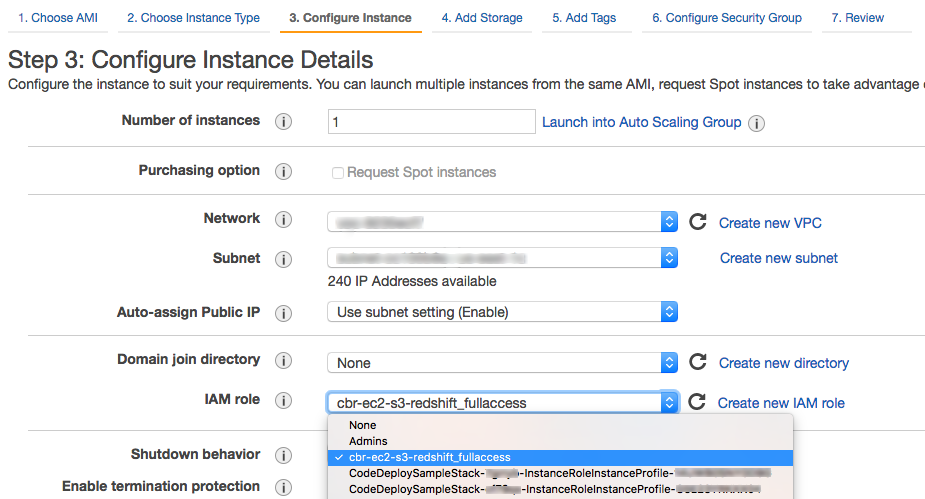
1. The IAM Role(s) can be created and attached at the time the CloudBasic instance is launched (in the given example a single role is used to facilitate access to S3, Redshift and SES):
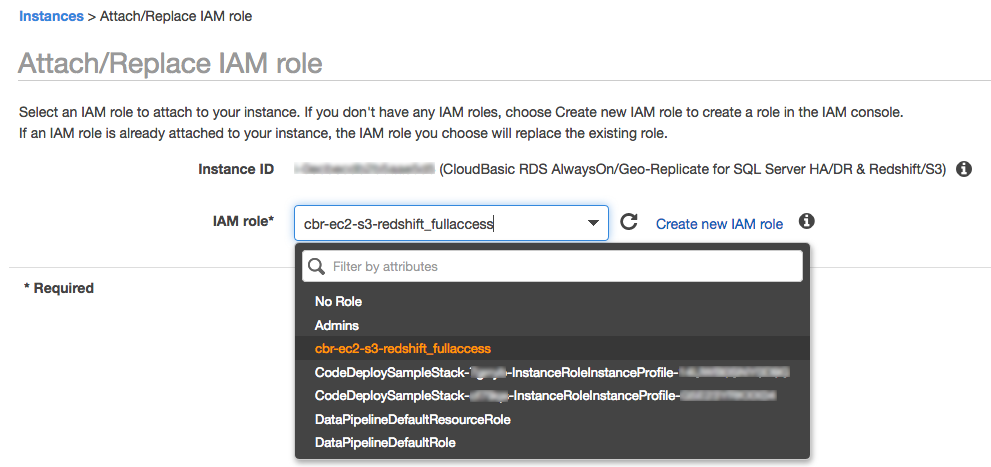
2. The IAM Role(s) can be attached to an already running CloudBasic EC2 instance:
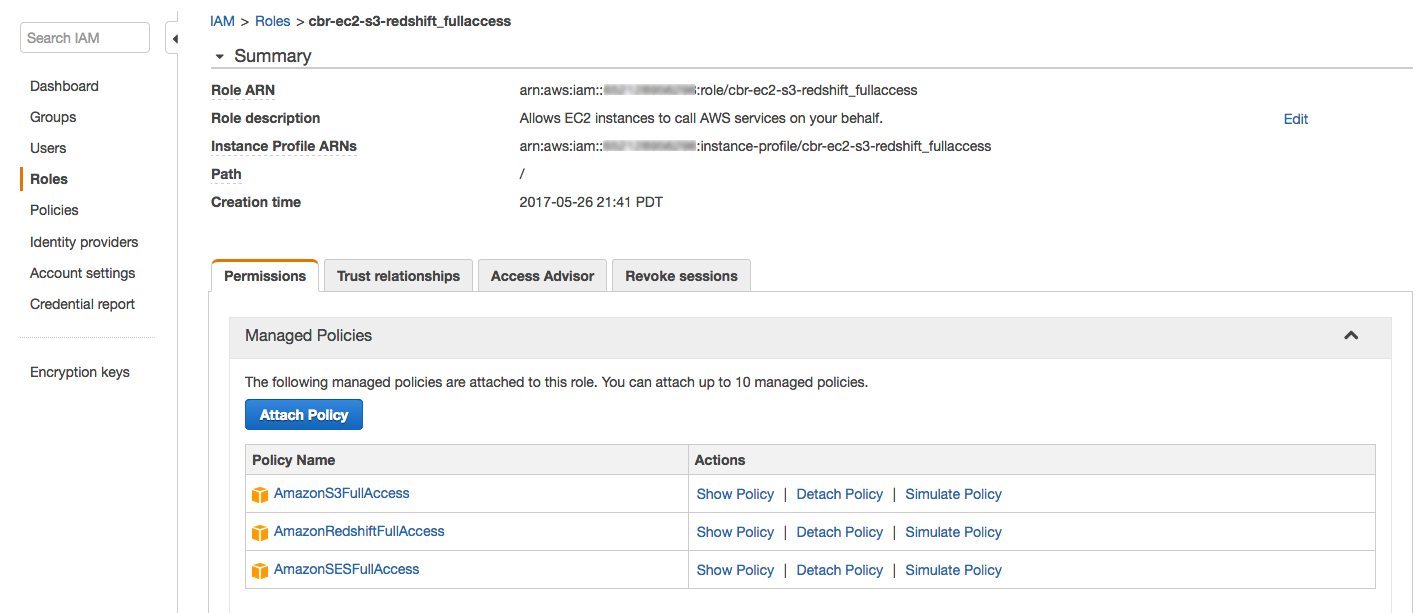
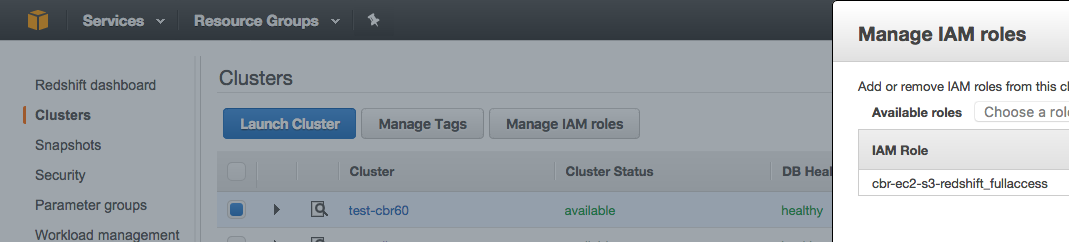
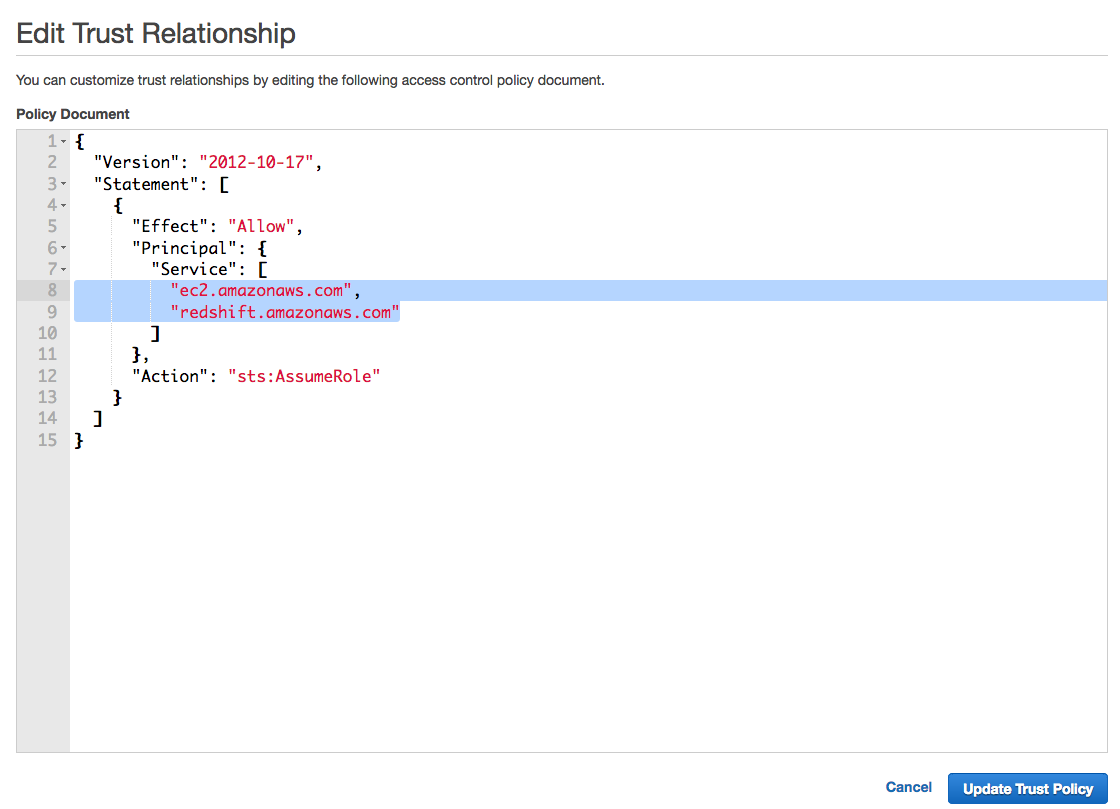
3. In addition to granting the IAM Role permission to Redshift, it needs to be also associated with the respective Redshift cluster. Note that the IAM role will be available to be associated with the cluster only if it a trust relationship between the IAM Role and Redshift is established (see the three screenshots below). For more information, visit the related AWS documentation section.
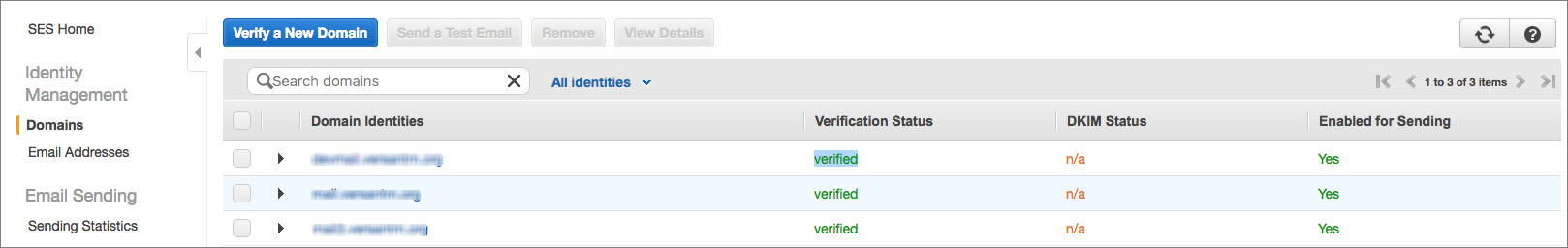
After granting the EC2 instance access to SES, there is one more step necessary to be completed, before you can configure email alerting under /Configuration - in the AWS Console, under SES, authorize the email (or the entire domain) that is going to be used as "Email From" email:
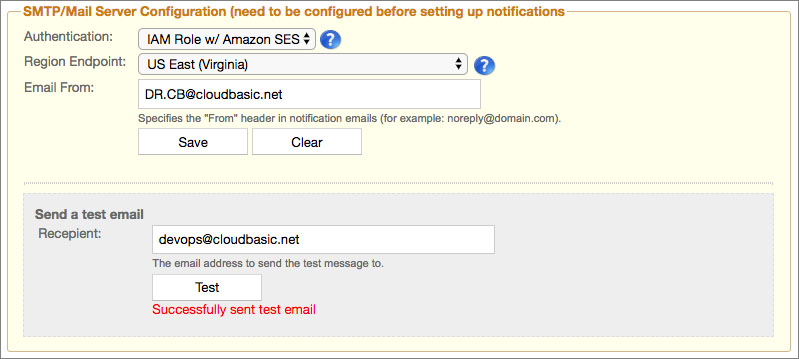
Then under /Configuration in the "SMTP/Mail Server Configuration" select the SES region and populate "Email From:" with the email authorized above. Test the configuration by sending a test email. Then you can proceed with configuring alerting under /Configuration.