Documentation
CloudBasic:
- What is CloudBasic:
- Most common scenarios:
- Using CloudBasic:
- Prerequisites
- Limitations
- Supported MS SQL Server Versions
- Deployment Guide (PDF)
- Release Notes
- Get Started - Configure Multi-AZ or Multi-AR with Readable Replicas
- SQL Server to SQL Server Replication
- SQL Server to Redshift
- SQL Server to S3 Data Lake
- Monitor a Continuous Copy Relationship
- Promote RDS/SQL Server Read-Replica to Primary
- Terminate a Continuous Copy Relationship
- Logs and Errors
- Warnings
- How To Upgrade
- Updating your version
- CloudBasic advanced features:
- Working in AWS:
- RDS Assemblies Activation Test
- RDS/SQL Server User Management
- RDS/SQL Server Backup and restore from/to S3
- RDS/SQL Server Snapshot-Restore
- VPN/VPC - Replication over VPN/VPC
- Compare Instance Types (Features & Support Details)
- How To Extend the Default Data Storage
- Attach IAM Role to EC2 and Redshift Cluster
- Deployment guide:
- Additional topics:
API Documentation:
- Default API Configuration
- Instance Management:
- User Management:
- Replication Management:
- CreateReplication
- CreateAllReplication
- GetReplicationsList
- ReplicationStatus
- AlterReplication
- DeleteReplication
- StartReplicationService
- StopReplicationService
- AnalyzeReplication
- CreateRedshiftReplication
- AlterRedshiftReplication
- DeleteRedshiftReplication
- CreateS3Replication
- AlterS3Replication
- DeleteS3Replication
- GetLogs
- RebuildDbReplicaIndexes
- RebuildDbReplicaIndexesStatus
- ReseedTable
- ReseedTableStatus
- Multi-AZ HA Cluster Management:
- Lambda/node.js Example:
- Disaster Recovery & No-Downtime Migration Management
- Service Management:
Encrypting Multi-AZ HA Cluster Communication
CloudBasic RDS AlwaysOn/Geo-Replicate for SQL Server HA/DR version 8.0 and above features encrypted communication between Multi-AZ High-Availability Cluster instance members. HTTPS/TLS 1.2 communication is handled over port 4431 (444 in versions 8 and 9; 4431 in version 10 and above).
Product version 10.0 and above
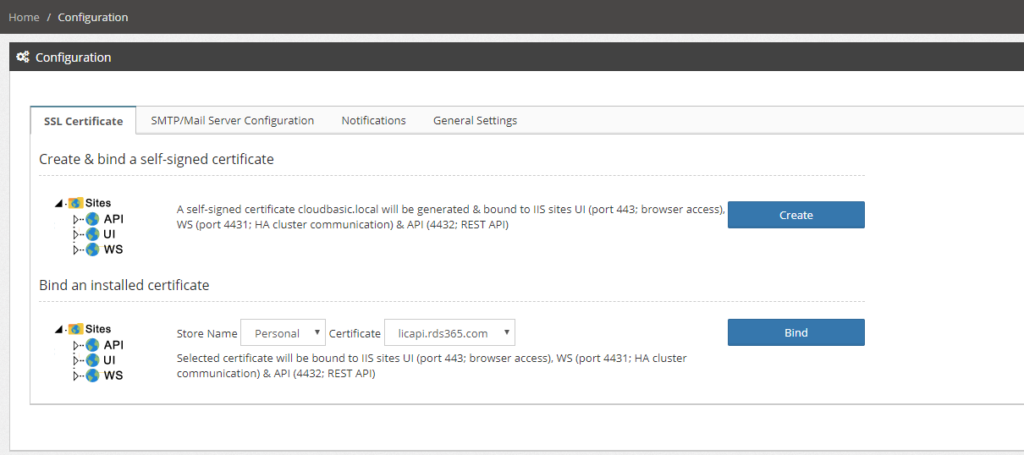
If securing Multi-AZ HA Cluster instances communication (port 4432) suffices (i.e. in test environment), a self-signed certificate can be generated and bound to the respective web server site WS (port 4431) with a click-of-a-button. Go to /Configuration, in the top section "SSL Certificate", click [Create]. Note that the same self-signed certificate cloudbasic.local will be bound to sites UI (port 443; browser console access) and API (port 4432; REST API) as well.
To install and bind a CA issued production certificate, RDP (remote desktop) to the CloudBasic Windows server, install the certificate into the Certificate Storage (default storage is [Personal]). Then go to /Configuration and click [Bind]. Note that the same certificate will be bound to sites UI (port 443; browser console access) and API (port 4432; REST API) as well.
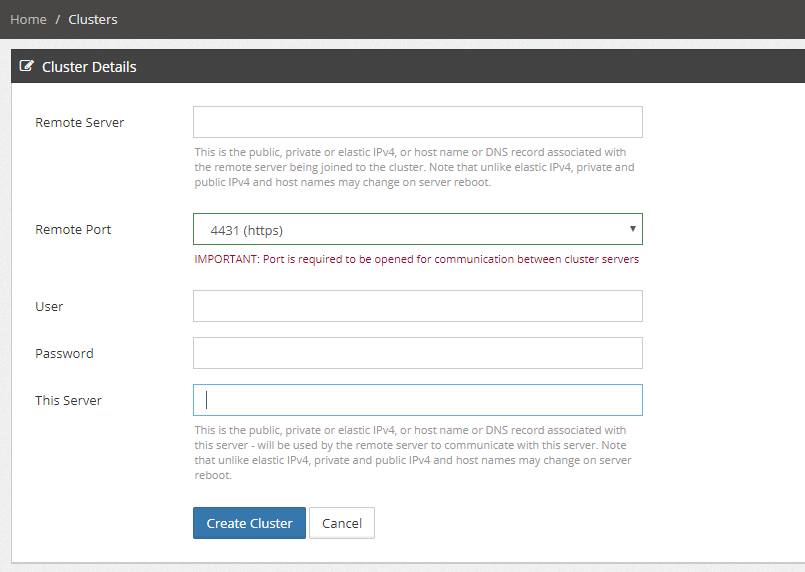
Under /Advnaced/Multi-AZ HA Cluster, select port 4431 (https) to activate cluster instance members communication over https TLS 1.2:
Product version 8.0 - 9.nn
In order to configure encrypted communication between HA Cluster members, install a self-signed or signed by a CA certificate on both cluster member instances (see below for instructions) and select the "(444/4431, https ..)" option:
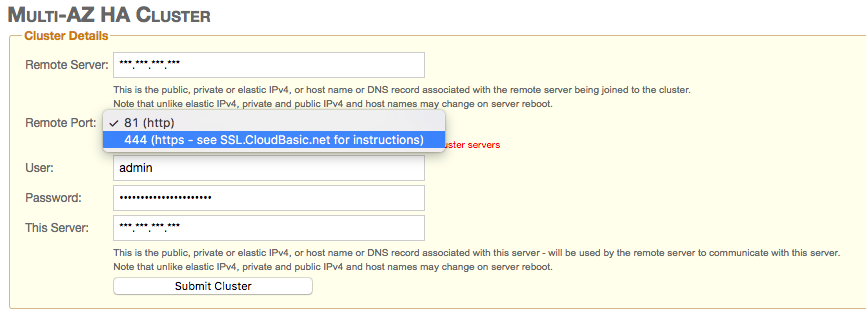
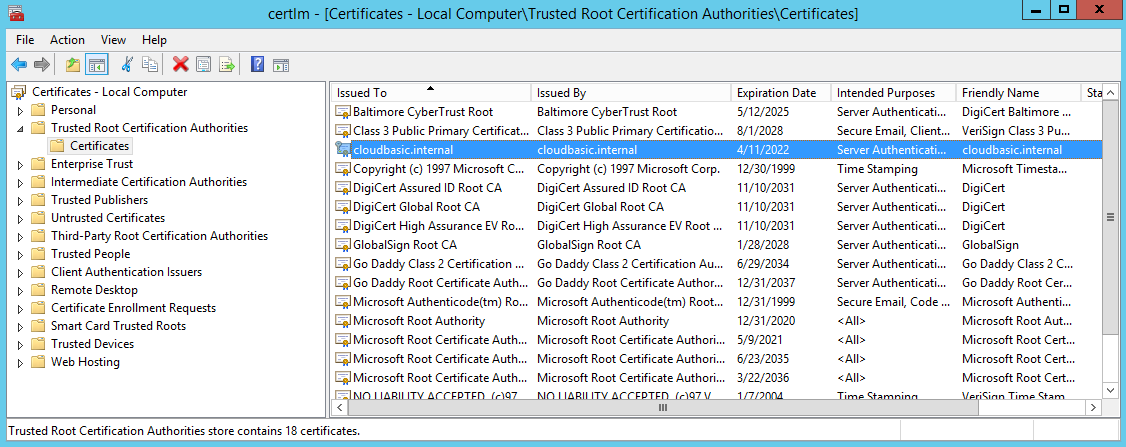
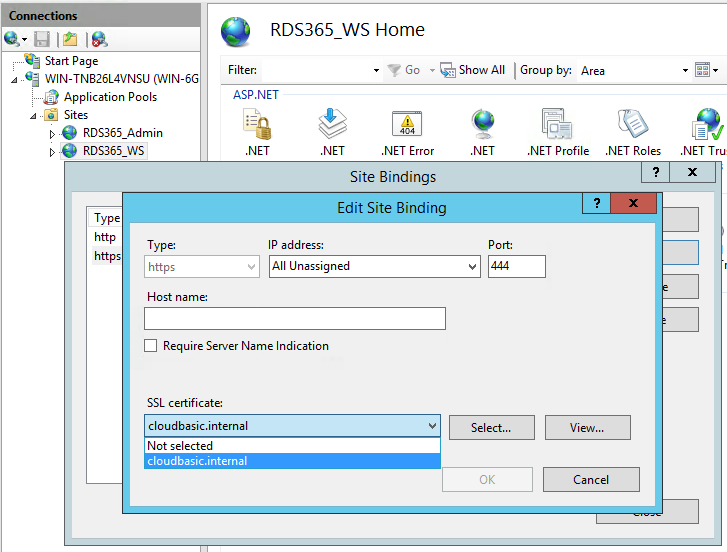
To install a certificate, RDP to the server, install your certificate into the trusted certificate storage, open the IIS manager, select RDS365_WS, then select binding, add https on port 444, select your certificate.
This is one example of how you can create a self-signed certificate using a PowerShell script:
RDP to the CloudBasic server, then execute below PowerShell command. A self-signed certificate will be created with default parameters, placed in certificate storage, and available for selection under IIS/RDS365_WS=>Binding
C:>PowerShell
PS> New-SelfSignedCertificate -certstorelocation cert:\localmachine\my -dnsname cloudbasic.internal
For more information, visit:
https://technet.microsoft.com/itpro/powershell/windows/pkiclient/new-selfsignedcertificate