Documentation
CloudBasic:
- What is CloudBasic:
- Most common scenarios:
- Using CloudBasic:
- Prerequisites
- Limitations
- Supported MS SQL Server Versions
- Deployment Guide (PDF)
- Release Notes
- Get Started - Configure Multi-AZ or Multi-AR with Readable Replicas
- SQL Server to SQL Server Replication
- SQL Server to Redshift
- SQL Server to S3 Data Lake
- Monitor a Continuous Copy Relationship
- Promote RDS/SQL Server Read-Replica to Primary
- Terminate a Continuous Copy Relationship
- Logs and Errors
- Warnings
- How To Upgrade
- Updating your version
- CloudBasic advanced features:
- Working in AWS:
- RDS Assemblies Activation Test
- RDS/SQL Server User Management
- RDS/SQL Server Backup and restore from/to S3
- RDS/SQL Server Snapshot-Restore
- VPN/VPC - Replication over VPN/VPC
- Compare Instance Types (Features & Support Details)
- How To Extend the Default Data Storage
- Attach IAM Role to EC2 and Redshift Cluster
- Deployment guide:
- Additional topics:
API Documentation:
- Default API Configuration
- Instance Management:
- User Management:
- Replication Management:
- CreateReplication
- CreateAllReplication
- GetReplicationsList
- ReplicationStatus
- AlterReplication
- DeleteReplication
- StartReplicationService
- StopReplicationService
- AnalyzeReplication
- CreateRedshiftReplication
- AlterRedshiftReplication
- DeleteRedshiftReplication
- CreateS3Replication
- AlterS3Replication
- DeleteS3Replication
- GetLogs
- RebuildDbReplicaIndexes
- RebuildDbReplicaIndexesStatus
- ReseedTable
- ReseedTableStatus
- Multi-AZ HA Cluster Management:
- Lambda/node.js Example:
- Disaster Recovery & No-Downtime Migration Management
- Service Management:
Encrypting Data In Transit
VPN is recommended for cross-region replications, but is not mandatory. Replications can be configured with data-in-transit encryption leveraging SQL Server level TLS/SSL encryption. For connections to SQL Server 2016 and above, TLS 1.2 is activated. For connections to SQL Server 2014 and below, TLS 1.1/1.0 or SSL is activated depending on the SQL Server version and applied updates. For more information see https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server
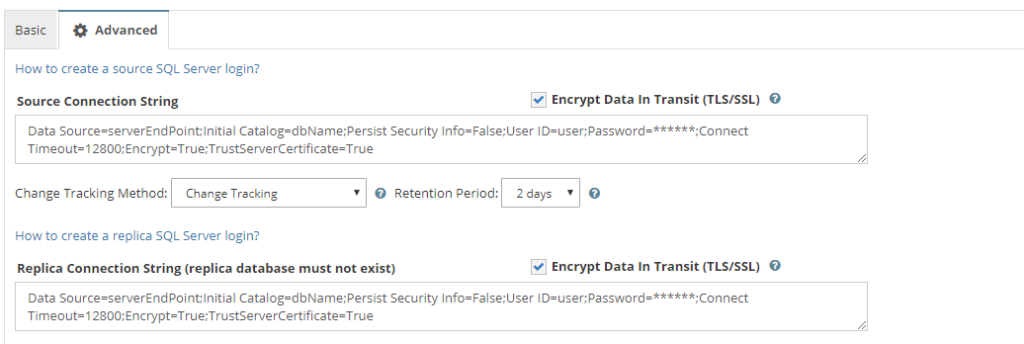
In CloudBasic 10.0 and above all connections are encrypted by default. In CloudBasic versions 9.11 and below, during configuration of a replication, go to Quick Setup, in the [Advanced Tab] select "Encrypt Data In Transit" for either the source, target or both connections.
For increased security, you may select to encrypt data in transit even if the CloudBasic instance, source and target SQL Servers are deployed within same VPC. Data in transit encryption introduces a negligible computational overhead.
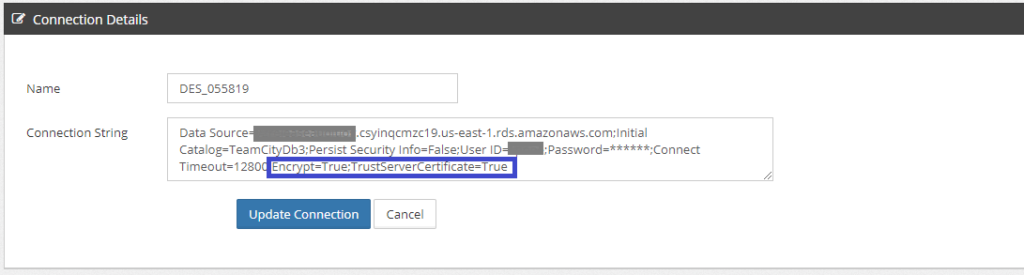
If a replication was initially configured without activating encryption, then to activate data in transit encryption, go to Advanced/Connection Strings, locate the respective source and/or target link, add "Encrypt=True;TrustServerCertificate=True".